Online advertising and traffic monetization are making billions of dollars yearly. Only at Adsterra, we cooperate with over 18K publishers and 12K advertisers who grow their business online. But with all advantages, all digital marketing actors face threats, as well. Cybercriminals are using advanced methods to hijack ads, replace IPs, and launder impressions. How can you protect yourself from malicious activities while doing business online? The AI-powered Adsterra malvertising protection ecosystem comprises hundreds of anti-malware algorithms and techniques. Today you will unveil how anti-malvertising works to protect your budgets and reputation from all types of offenders and their harmful activities.
Adsterra Malvertising Official Statement
To begin with, we must declare our position concerning any type of violative activities against Adsterra or its partners. As stated in the Adsterra Terms and Conditions, we prohibit any type of malvertising and irrevocably ban all types of offensive content, including:
- malware and unlawful software;
- phishing;
- prohibited offer types;
- illegal advertising;
- URLs and tracking links switching, and many more including those listed in our knowledge base.
What is malvertising and how can it harm businesses?
Cybercriminals can disrupt online advertising by attacking advertisers, publishers, and ad networks by spreading malware. This process is called malvertising and it can wreck a publisher’s reputation as a traffic source, drain marketing budgets, and severely harm users’ devices (if talking about viruses).
The goal of attackers is either to break into a user’s computer system (PC, laptop, smartphone, even IoT devices) to execute virus programs, or to phish credentials or payment data.
Malvertising vs. Adware
Malvertising is commonly mixed with ad malware. Adware is executed on a user’s computer without their permission. Usually, it is aimed at affecting a victim’s software or browsers. Adware can switch search engines, redirect users to third-party advertising, as well as collect user data.
While malvertising is deployed on an infected source and affects multiple users who click on ads, adware is placed on the end user computer or smartphone. The types you may have heard of:
- viruses;
- trojans;
- spyware (aims at accessing to private information such as passwords, bank details);
- ransomware (encrypts files on a user’s machine and locks the access to all files asking for a ransom);
- other malicious software packages.
Malvertising vs. Ad fraud
While many authors use these words as interchangeable, there is a critical difference between them. Ad fraud relates to low-quality traffic and all connected unwanted activities to imitate real users’ actions:
- impressions fraud;
- click fraud;
- conversion fraud;
- cookies’ fraud, etc.
These are marketers and brands who suffer from those abusive techniques. Please read a guide to all-round anti-fraud protection for our advertisers and affiliates.
Malvertising relates to ad quality and these are publishers who suffer from deliberate attacks to their inventory.
Now let’s carry on with how unwanted, fake ads can compromise users and publishers.
How can malvertising disrupt users?
Fake codes, when invoked on a web page, can redirect users to malicious websites.
Malvertisements can execute hidden codes that will install adware to a user’s computer or smartphone.
Phishing attacks: when a user is redirected to a fake website that collects personal information including credit card details.
How malvertisements harm publishers
While users suffer from losing control over their computers or face their payment details stolen by attackers, publishers struggle with other threats.
- Advertising networks and affiliate platforms ban publishers who they suspect in spreading malware.
- Advertisers blacklist publishers with massive low-quality traffic that can be inflated with bots.
- Finally, publishers risk losing their reputation, traffic volumes, and revenues.
Most common malvertising methods you should know
Having outlined what malvertising is, we now move to listing the most common threats that advertisers and publishers face. This will help in better understanding of how these unwanted activities are prevented and blocked.
The “ad call” malvertising
Publishers place scripts that they take from ad networks on their websites and mobile apps. The networks send ads to these scripts via several third party servers. One of these servers can be attacked, which allows the perpetrator to apply malicious codes to ad feed. That’s why Adsterra uses in-house systems to constantly monitor all servers’ responses and allows only clean feed.
Malware inside a landing page
Users click on some banners or pop-ups, follow to the landing page where they meet…a malicious code that starts executing right away. Even legitimate landing pages of premium advertisers can be attacked by such codes.
Post-click malware
This type of attack happens after a user’s click. Instead of reaching a target landing page, users are redirected to a fake source. How does it happen? Attackers can meddle in the ad delivery process, switching the URLs.
Adsterra scans not only landing pages and prelanders but also all ad delivery paths to prevent post-click attacks.
Malvertisements inside advertising creatives
These unprincipled activities are mostly intended. Attackers can register with an ad network and upload creatives containing malicious codes. Therefore, publishers need to choose reputable monetization platforms that deliver all-round security of their inventory.
There are many other types of malvertising that you can read about on the Internet. But even armed with this list you can imagine how important it is to have a 360-degree protection from malicious codes.
Adsterra malvertising protection techniques
We have outlined how malicious ad codes can infect ads and redirect users to phishing pages or download and execute harmful adware on users’ computers. Malware spreading is tightly connected with breaches in publishers’ inventory and ad networks’ security systems.
Over 18K direct publishers trust Adsterra when it comes to safe online monetization. We protect them from possible unreliable advertisers and block attempts to compromise their websites with malware.
How Adsterra malvertising protection techniques work
Protecting Adsterra premises would not be enough here. Hence, we developed a multy-level and multi-layered ecosystem to control every stage of online advertising. Let’s outline the most important parts of how the ecosystem provides all-round protection.
RESEARCH & SYSTEM UPGRADING
- Researching malicious codes
- Training AI algorithms on new datasets
- New anti-malware algorithms testing
- Security infrastructure modernization
- Upgrading server security
- Hiring and training experienced Policy Team
PUBLISHERS: MALWARE PREVENTION & COMBATING
Real-time monitoring
- New accounts multi-stage verification
- Ad creatives scanning (newly-added and existing)
- Prelanders scanning (newly-added and existing)
- Landing pages scanning (newly-added and existing)
- Protection against: ad call, post-click, in-lander, in-video, in-creative malware.
ADVERTISERS: AD FRAUD PREVENTION & COMBATING
Real-time monitoring
- All-round websites’ scanning
- Traffic scanning
- Conversions and clicks checking
- Possible redirect detection
- Protection against: URL switching, GEO spoofing, impression fraud, click fraud, conversion fraud, incent traffic.
IN-NETWORK: ALL-ROUND PREMISES PROTECTION
- Data centers and infrastructure security
- Secured servers and SSL data transmission
- All transactions encryption using industry-standard technology
- Payment security
- Encryption of all communications

When legitimate ads can be seen as malvertising or viruses
Malvertising can be versatile, but not every ad is bad even if it seems so. What does it mean? From time to time, publishers report malware or virus ads on their websites but these are nothing but specific ad creatives.
There are tons of software and phone utilities promos running within ad networks. To make users click, advertisers and marketers need to come up with catchy visuals (aka creatives). Sometimes, these creatives are too pushy but still, non-misleading.
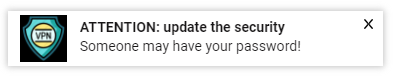
Like in this case below, when we see an ad creative of anti-virus software. The heading is urging viewers to update the security software as their credentials might be under danger. That’s nothing but the ad heading, but some publishers get concerned when their websites show notifications like this one.
How to make credible ad creatives with high CTRs
We at Adsterra always recommend to be delicate and genuine in creatives’ slogans and designs. We publish guides to making up effective creatives that won’t shock users but rather convert into many leads. Our partners share case studies where they demonstrate how to urge users to scare them away with, say, VPN and anti-viruses ads. However, there always will be advertisers who prefer flashy headings and aggressive call-to-action moves.
The best and the right thing to do when you see a dubious creative is to report to the Adsterra Support team. We will check any ad campaign on request.
Conclusion
Summarizing all mentioned above, let’s list the main points:
- Unlawful techniques can fabricate impressions, clicks, and conversions. This is called ad fraud. Ad fraud methods are harmful for advertisers as they are spending their budgets on fake traffic.
- Malicious codes can integrate into ad creatives, landing pages, videos, as well as replacing legitimate websites with false ones. They are used to disrupt users’ computers, steal personal and payment data, wreck publishers’ websites. This is called malvertising.
- Before you start cooperating with ad networks as an advertiser or a publisher, make sure they provide you with a fully-fledged security system: from SSL connection to in-house malware monitoring algorithms.
Adsterra malvertising protection and prevention ecosystem is ever-evolving. We provide cutting-edge security for all partners, advertisers, publishers, and affiliates. Stay safe and make money!
